Summon a ghostwriter
everywhere you type
Summon a shakespeare
For when the words have to land.

"No one tells you that LinkedIn growth = writing comments on other people’s posts every day. Hover cuts that down to minutes while actually growing the business."

George YanPresident at Hankow Food Inc.
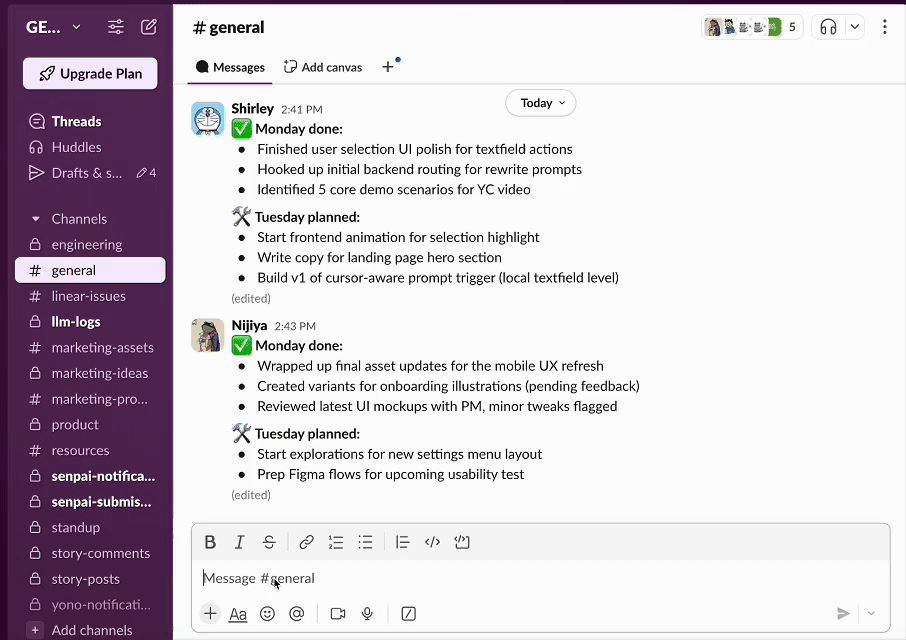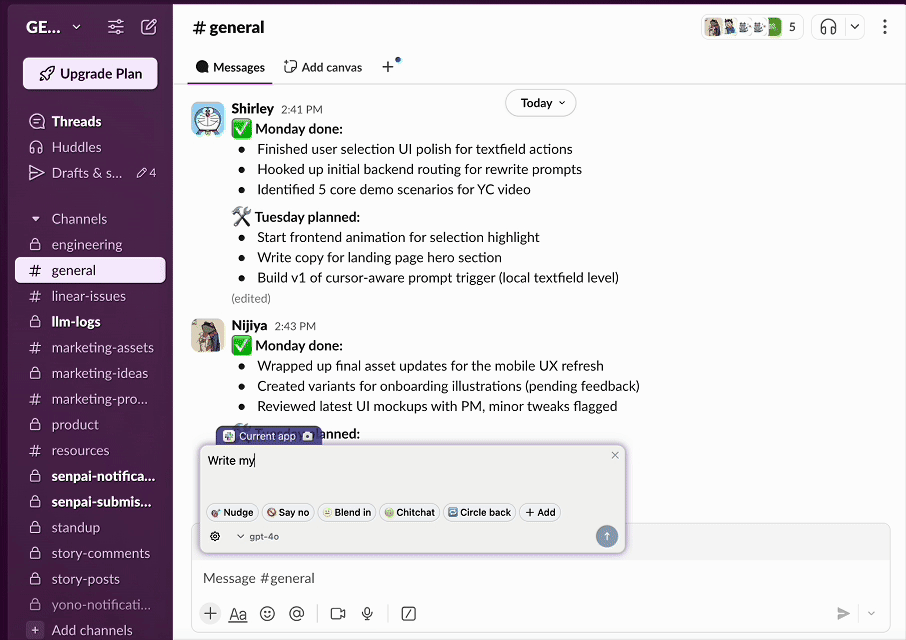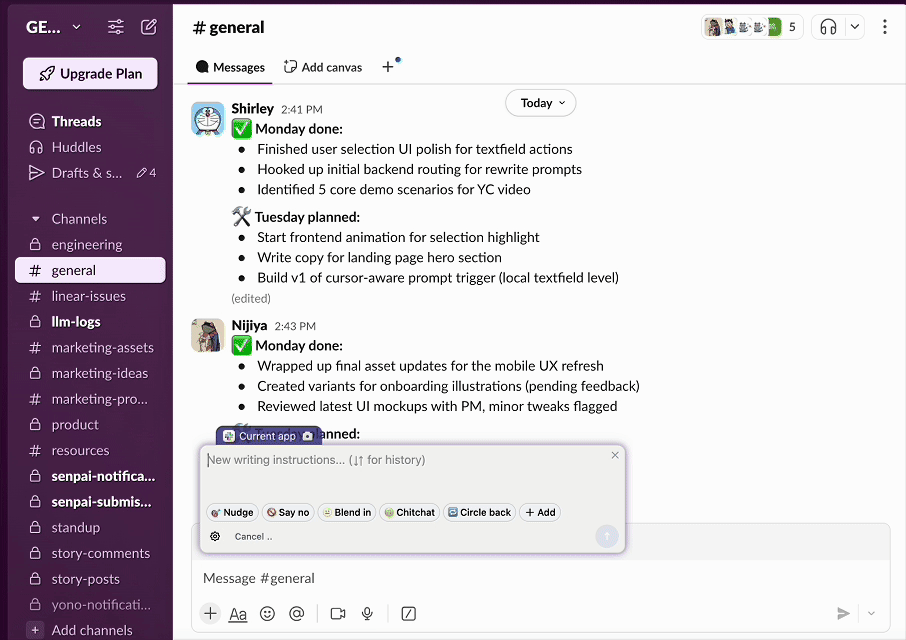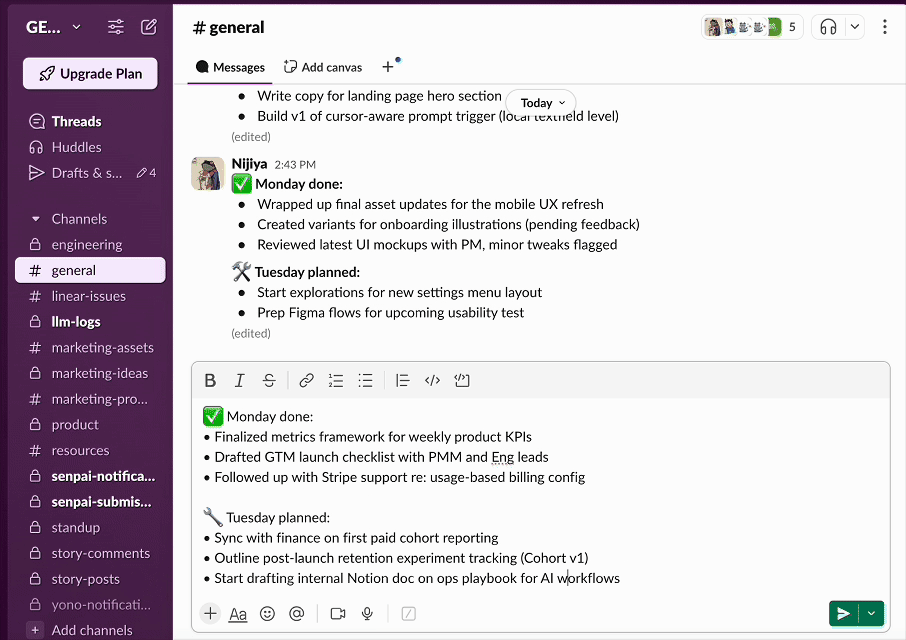
Turn Every Text Field Into |
🎯 No more copy-pasting and tab-switching because HoverGPT:
- • Sees what you're working on (you can turn it off)
- • Knows where your cursor is
- • Knows what your selection is
- • Writes, rewrites, or edits inline
- • Works in Gmail, Slack, Chrome - anywhere on your computer

Your voice, perfected for every platform
Hover lets you define multiple versions of you by writing your ownsystem promptsfor your favorite apps
Personalize for
Slack
X (Twitter)
Tinder
LinkedIn
Microsoft
Gmail
Discord
Notion
Linear
Telegram
Obsidian
Define your own
- •System prompts
- •Shortcut actions
- •Workflows (coming soon)
- •Clipboard (coming soon)

All that. Replaced for$16and one universal shortcut.
Security is important to you. Us too.
What happens on your screen stays on your screen.
How HoverGPT Uses Your Screen Data
When you call HoverGPT, it captures your screen context on your behalf, just like manually taking a screenshot and pasting it into ChatGPT. Except for HoverGPT does it instantly.
You Decide What's Shared
Choose whether to include screen data in your request.
No Storage or Middleman
When you call a model (like OpenAI), your data is sent directly to that provider for processing and not retained by HoverGPT. We save your recent 5 prompts locally so you can quickly reuse them.
Local-only Mode
Need full privacy? Enable Local-Only Mode to restrict HoverGPT to on-device models (like Llama 3). No screenshots or data leave your Mac, ever. Perfect for sensitive work.
Coming Soon
Bring Your Own Key
HoverGPT doesn't proxy your requests: it uses your own OpenAI, Anthropic, or other API keys directly.
Coming Soon
SOC 2 (Type 2)
HoverGPT's infrastructure is SOC 2 Type 2 certified, meaning independent auditors verify our security controls—data encryption, access logging, and strict internal policies.